FlexibleIR Automation
FlexibleIR Automation
Flexible IR adopts a clear framework to identify tasks for automation. We track every TASK done during an Incident. This data helps to clearly identify what tasks needs to be automated.
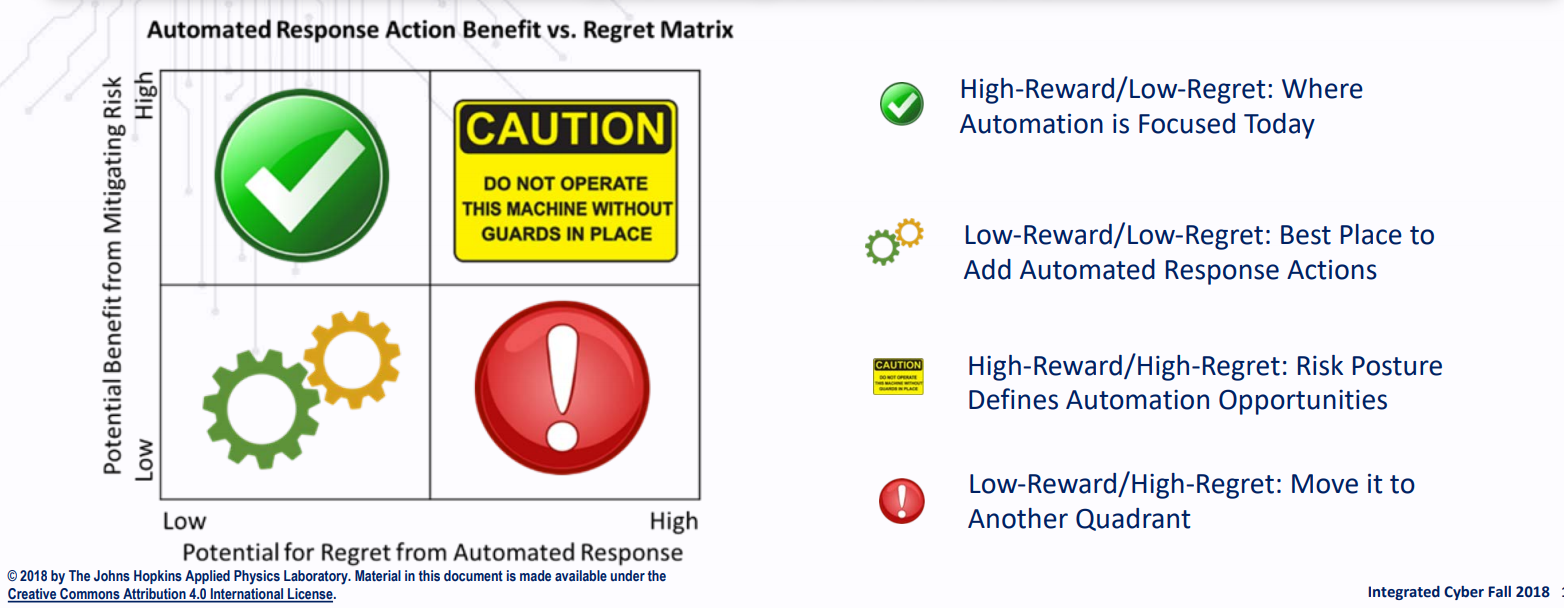
IACD recommends enterprises to Focus on identification and execution of high-reward / low regret response actions.
What do we automate?
What do we automate?
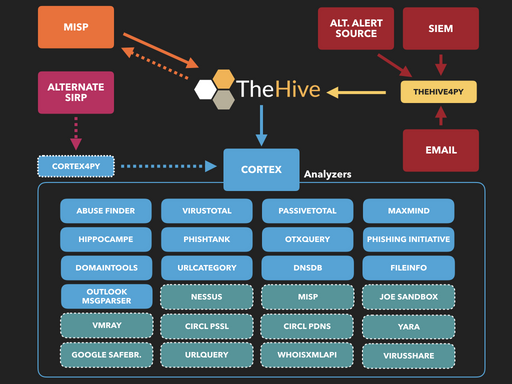
- Incident enrichment - Based on the artifacts available for the case, we programatically check with external service providers. For eg domain, url, IP address, File checked with virustotal. We also integrate with Cortex (Analyser part of theHive project) which has around 70 external analysers.
- Integration with internal systems for automated ticket creation/updation etc. API support being the key here for integration.
- Automated partial classification (only the type - eg - DoS or Malware attack) of an incoming IR event. Purely based on the data set available in the company. Machine learning libraries used - Python SciKit libraries + NLP.
- Automated search of past cases - ELK integration where every case data with Indicators of compromise (IoC) gets into Elasticsearch.
- Integration with collection systems/agents that exist in the company(mainly application performance management - APM tools). Will help in quick information retrieval during IR handling.
- Automated approved remediation - Eg - If an anomaly detected by an end point device and a corresponding Incident raised in Flexible IR. Based on analysts decision Block the IP address by writing a firewall rule. This is purely based on the authentication to the Firewall and the APIs provided by the Firewall device.
Contact
Contact
Your message is important to us. We will ensure to get back within 24 hours.
Email Us
contact@flexibleir.com